B.5. Exporting your Public Key
Before you can use public key cryptography, other people must have a copy of your public key. To send your key to correspondents or to a keyserver, you must export the key.
To export your key, so you can display it on a webpage or paste it in email, type the following command:
gpg --armor --export <you@example.com> > mykey.asc |
You will not see any output, because not only did you export your public key, you redirected the output to a file called, for example, mykey.asc. (Without the addition of > mykey.asc, the key would have been displayed as the standard output on the monitor screen.)
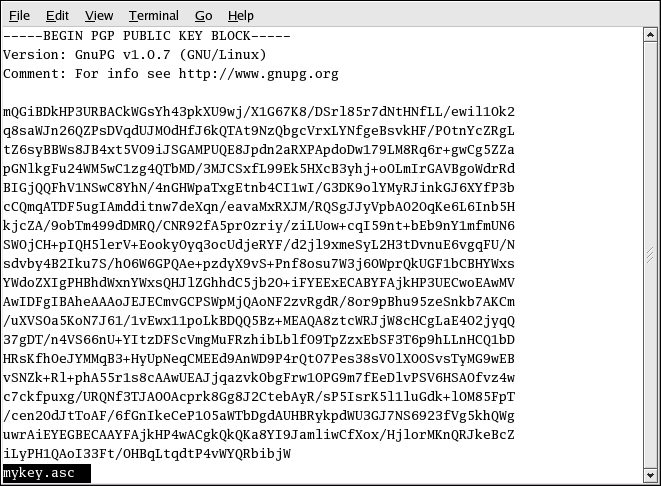
Now, the file mykey.asc can be inserted into email
or exported to a keyserver. To see the key, type less
mykey.asc to open the file in a pager (type
-----BEGIN PGP PUBLIC KEY BLOCK----- Version: GnuPG v1.0.1 (GNU/Linux) Comment: For info see http://www.gnupg.org mQGiBDkHP3URBACkWGsYh43pkXU9wj/X1G67K8/DSrl85r7dNtHNfLL/ewil10k2 q8saWJn26QZPsDVqdUJMOdHfJ6kQTAt9NzQbgcVrxLYNfgeBsvkHF/POtnYcZRgL tZ6syBBWs8JB4xt5V09iJSGAMPUQE8Jpdn2aRXPApdoDw179LM8Rq6r+gwCg5ZZa pGNlkgFu24WM5wC1zg4QTbMD/3MJCSxfL99Ek5HXcB3yhj+o0LmIrGAVBgoWdrRd BIGjQQFhV1NSwC8YhN/4nGHWpaTxgEtnb4CI1wI/G3DK9olYMyRJinkGJ6XYfP3b cCQmqATDF5ugIAmdditnw7deXqn/eavaMxRXJM/RQSgJJyVpbAO2OqKe6L6Inb5H kjcZA/9obTm499dDMRQ/CNR92fA5pr0zriy/ziLUow+cqI59nt+bEb9nY1mfmUN6 SW0jCH+pIQH5lerV+EookyOyq3ocUdjeRYF/d2jl9xmeSyL2H3tDvnuE6vgqFU/N sdvby4B2Iku7S/h06W6GPQAe+pzdyX9vS+Pnf8osu7W3j60WprQkUGF1bCBHYWxs YWdoZXIgPHBhdWxnYWxsQHJlZGhhdC5jb20+iFYEExECABYFAjkHP3UECwoEAwMV AwIDFgIBAheAAAoJEJECmvGCPSWpMjQAoNF2zvRgdR/8or9pBhu95zeSnkb7AKCm /uXVS0a5KoN7J61/1vEwx11poLkBDQQ5Bz+MEAQA8ztcWRJjW8cHCgLaE402jyqQ 37gDT/n4VS66nU+YItzDFScVmgMuFRzhibLblfO9TpZzxEbSF3T6p9hLLnHCQ1bD HRsKfh0eJYMMqB3+HyUpNeqCMEEd9AnWD9P4rQtO7Pes38sV0lX0OSvsTyMG9wEB vSNZk+Rl+phA55r1s8cAAwUEAJjqazvk0bgFrw1OPG9m7fEeDlvPSV6HSA0fvz4w c7ckfpuxg/URQNf3TJA00Acprk8Gg8J2CtebAyR/sP5IsrK5l1luGdk+l0M85FpT /cen2OdJtToAF/6fGnIkeCeP1O5aWTbDgdAUHBRykpdWU3GJ7NS6923fVg5khQWg uwrAiEYEGBECAAYFAjkHP4wACgkQkQKa8YI9JamliwCfXox/HjlorMKnQRJkeBcZ iLyPH1QAoI33Ft/0HBqLtqdtP4vWYQRbibjW =BMEc -----END PGP PUBLIC KEY BLOCK----- |
B.5.1. Exporting to a Keyserver
If you are only writing to a few correspondents, you can export your public key and send it to them personally. If you correspond with many people, however, distribution of your key can be time consuming. Instead, you can use a keyserver.
A keyserver is a repository on the Internet which can store and distribute your public key to anyone who requests it. Many keyservers are available, and most try to remain synchronized with each other; sending your key to one keyserver is like distributing it to them all. A correspondent can request your public key from a from a keyserver, import that key to their keyring, and they are ready for secure correspondence with you.
 | Tip |
|---|---|
Because most keyservers are synchronized, sending your public key to one keyserver is usually as good as sending it to them all. You can, however, locate different keyservers. One place to begin your search for keyservers and more information is Keyserver.Net available at http://www.keyserver.net. |
You can send your public key from either the shell prompt or from a browser; of course, you must be online to send or receive keys from a keyserver.
From the shell prompt, type the following:
gpg --keyserver search.keyserver.net --send-key you@example.com
From your browser, go to Keyserver.Net (http://www.keyserver.net) and select the option to add your own PGP public key.
Your next task is to copy and paste your public key into the appropriate area on the webpage. If you need instructions on how to do that, use the following:
Open your exported public key file (such as mykey.asc, which was created in Section B.5 Exporting your Public Key) with a pager — for example, use the less mykey.asc command.
Using your mouse, copy the file by highlighting all the lines from the BEGIN PGP to END PGP notations (see Figure B-1).
Paste the contents of the file mykey.asc into the appropriate area of the page on Keyserver.Net by middle-clicking with your mouse (or left- and right-clicking if you are using a two-button mouse). Then select the Submit button on the keyserver page. (If you make a mistake, press the Reset button on the page to clear your pasted key.)
Note that if you are submitting your key to another Web-based keyserver, the above transaction will be essentially the same.
That is all you need to do. Regardless of whether you use the shell prompt or the Web, you will see a message that your key was successfully submitted — either at the shell prompt or at the keyserver's website. From now on, users who want to communicate securely with you can import your public key and add it to their keyring.